One of the ways many people today are using Virtual Private Network, also known as a “VPN” is something you are hearing about often now likely. You are likely seeing that is protects you from bad guys (aka the ever present “Hacker”) but just how does a VPN work?
The technology which would become the VPN started their life 25 years ago at Microsoft as part of Windows 95. The problem which was being solved was the case where someone who worked for an organization who was traveling or located in a remote office who needed to securely connect to their home office. While you could spend huge amount of money to get a dedicated direct physical connection between the two locations using the already existing worldwide Internet was a great way to go. Effectively the team came up with the notion of creating a virtual dedicated line between two points. This became known a s PPTP- Point to Point Tunneling Protocol. The way PPTP works is creating an encrypted connection between the remote user and the home office.
A standard Internet Connection with no VPN
What is a tunnel?
A VPN is just the next step in evolution of PPTN, the general way it works is a remote individual connects to a VPN server in a specific location. That connection is secure using encryption, they any other connections done are done from the VPN Server. Again, the notion of the “tunnel” is like a virtual cable going from your computer to the VPN Server Selected. The obvious use of the tunnel is security, if you and work are both connecting to a VPN server you have a virtual connection from you to work. So a Virtual Private Network is just that, you can access resources at work from the other side the world with the ease you would from inside the office.
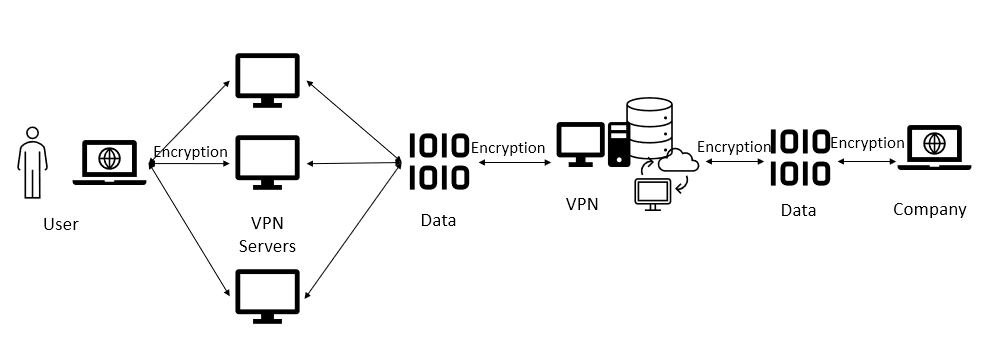
Using a VPN as a corporate user
Benefits of a VPN
As you have encryption that means it’s much more difficult for bad guys to see your data, it’ll also prevent your ISP, or any organization for that matter with the sole exception of the VPN provider, from seeing your activity. It also makes targeted marketing difficult as internet advertisers will have no idea who you are and where you are coming from. Interestingly many private individuals have realized they would like some of those benefits. In the last few years, we have seen a spate of companies starting up to provide VPN services for anyone and they are pretty in expensive.
VPN’s for everyone
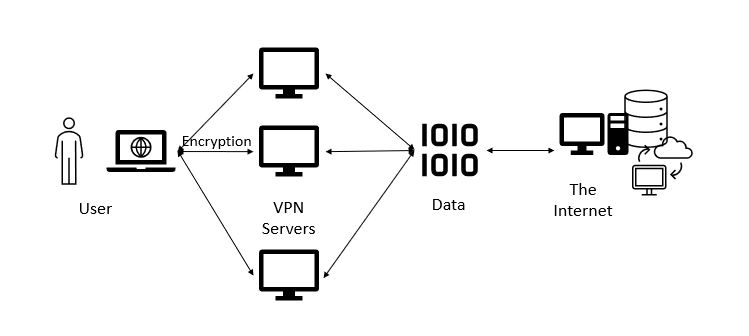
A non-corporate connection to the Internet using a VPN Server- you can have a range of servers to choose from
These works just like their corporate cousins with the exception that you effectively connect to the internet from the VPN server you choose. The “other end” of the connection is simply the internet versus a corporation. There are added benefits, a major one is regarding streaming services which restrict content depending on where you are located you can simply identify a VPN Server.
There are some other great benefits, if you use a VPN connected to a specific country products or services could be priced much lower than where you are. Airline tickets are a well known opportunity to connect to one country via a VPN to get better prices. I will note that as time goes on it’s more likely that merchants of all shapes and sizes will begin to identify popular VPN services and close these holes. In some countries where free speech is not guaranteed, a VPN could be a way to embrace free speech but at a risk to personal safety.
There are some less serious reasons to use a personal VPN-say you want to see the new episode of “Staged” from the BBC but you are in North America, you can select a server in the UK and the BBC would allow you to watch the episode as opposed to waiting for it to come to a streaming service in North America.

Looking at the BBC from North America
As an example, you can see that he BBC main page is quite different when connecting from North America versus the UK, as in the second instance a VPN was used to connect to the UK. You will notice that the websites are similar but quite different.

Looking at the BBC Website using a VPN in the UK from North America
I hope this has helped give you a quick overview on VPNs, why people use them and can help you to identify if you wish to use one or not. They are not awfully expensive for private individuals and are becoming much more popular. Using one all the time, just connect to your own country, is not a bad way to go as it is still a more secure way to browse the web. There will be minor lag triggered due to the encryption, but you will not notice it under normal browsing conditions. Most personal VPN companies offer a free trial, give it a spin!


