In the vast expanse of the internet, a section lurks in the shadows, often misunderstood and shrouded in mystery: the dark web. This article aims to demystify this hidden segment of the digital world, exploring its history, uses, and the threats it poses, as well as the reasons why individuals may venture into this digital abyss.
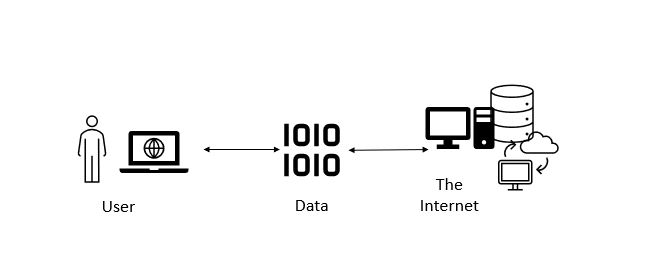
So Just What is the Dark Web? The dark web is a part of the internet that isn’t indexed by standard search engines like Google or Bing. Accessible only through special software like Tor, which anonymizes users’ identities and locations, the dark web is often associated with a variety of illegal activities. However, it’s important to understand that it also serves as a haven for legitimate, privacy-seeking activities, especially in countries where free speech is restricted. The origins of the dark web are closely linked to the development of the Tor network, originally created by the United States Naval Research Laboratory in the mid-1990s. It was designed to protect intelligence communications online. The Tor browser, released to the public in 2002, repurposed this technology for broader use, inadvertently paving the way for the dark web’s emergence.
Contrary to popular belief, the dark web isn’t solely a hub for criminal activity. It’s a complex ecosystem with both nefarious and noble uses. Are there wild rumors about what you can do? By all means there are, but I really do think they are at least partially fiction. Some examples of very real, horrible observed activities which the Dark web can support”
- Cybercrime: The dark web is a hotbed for cybercriminal activities. It hosts markets for buying and selling malware, exploit kits, and stolen data, including credit card information, personal identification, and login credentials.
- Drug Trafficking: One of the most common uses of the dark web is the sale of illegal drugs. Marketplaces like the now-defunct Silk Road popularized this trend, operating much like legitimate e-commerce sites but for controlled substances.
- Weapons Trade: The anonymity of the dark web also facilitates the sale of illegal firearms. These transactions, devoid of regulatory oversight, pose significant challenges to law enforcement agencies.
- Human Trafficking and Exploitation: Perhaps the most abhorrent of its uses, the dark web has been used for human trafficking and sharing exploitative content, often evading standard law enforcement techniques due to its encrypted nature.
There is a downside, a big one: the anonymity of the dark web makes it a breeding ground for illegal transactions, including drug trafficking, weapons sales, and cybercrime. Notorious examples include Silk Road, a black market for drugs, and AlphaBay, a marketplace for all sorts of illegal goods and services.
This activity can be countered by good and noble uses of the Dark web. People striving for freedom where governments try to suppress free speech are very much aided by it. In those cases the dark web provides a platform to share information without fear of reprisal. Platforms like SecureDrop allow individuals to share sensitive information with media organizations anonymously. Some specific examples of activities for good the Dark web supports are:
- Safe Haven for Whistleblowers: Platforms like SecureDrop are dedicated to allowing whistleblowers to share information with journalists securely. This aspect of the dark web is vital in regimes where freedom of speech is suppressed and whistleblowing can lead to severe repercussions.
- Tool for Journalists and Activists: In countries with heavy censorship and surveillance, the dark web provides a platform for journalists and activists to communicate and share information anonymously, evading government monitoring and censorship.
- Privacy Protection: For individuals concerned about privacy and surveillance in the digital age, the dark web offers an alternative to the surveillance-ridden ‘surface web’. It allows users to communicate, share, and browse with a significantly higher degree of anonymity.
- Access to Censored Information: In some regions, the dark web is a crucial tool for accessing information censored by authoritarian governments, including news sites, political discussions, and cultural content
An example of good which comes to mind is to Imagine a political activist in an oppressive regime, seeking to communicate with journalists without risking their safety. They turn to the dark web, using secure messaging services to share their story. In another scenario, a cybersecurity researcher delves into the dark web to study the latest malware trends, contributing valuable knowledge to the field of digital security.
The dark web poses significant challenges to law enforcement and national security. The anonymity it offers helps mask the identities of individuals involved in illegal activities, making it difficult to track and prosecute offenders. Additionally, it’s a fertile ground for the proliferation of malware and the exchange of stolen data, contributing to the global issue of cybersecurity. It is very much a quandary as the existence of the dark web presents a complex moral and ethical puzzle. It’s a digital embodiment of the age-old debate between liberty and security. On one hand, its potential for facilitating criminal activities demands stringent oversight and control. On the other, its role in protecting privacy, free speech, and access to information in oppressive regimes is invaluable.
I remember writing an article 25 years ago about how (as it was often know) “The Web ” itself had strong positive and negative potential, it’s just how you use it. The Darknet is after all, just a different type of Internet server and those pluses and misuse are magnified in a universe of anonymity.
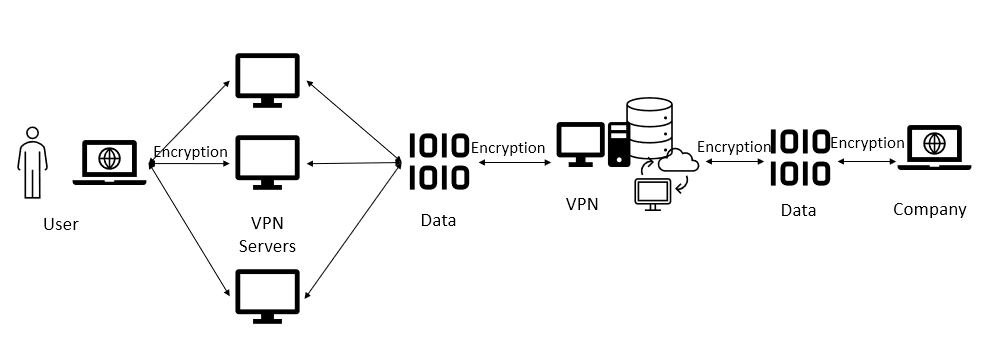
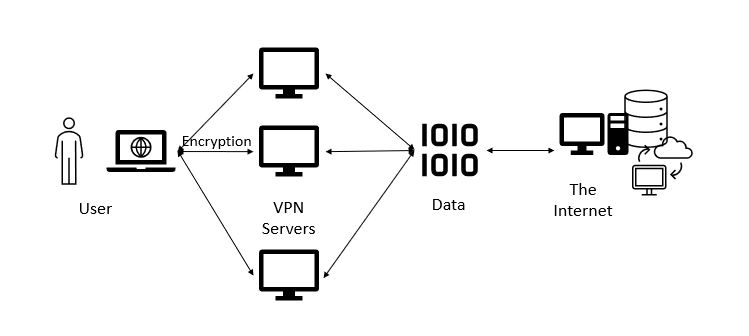
Is it easy to access the dark web? It actually is, now there are multiple ways to go about it, but taking steps to maintain anonymity are critical. I’m a cybersecurity professional, I literally make a living thinking about how things can go wrong, so I would take multiple layers of precaution using specific software (VPN software or Virtual Private Network, the Tor browser, which routes internet traffic through multiple servers to anonymize it for starters). Some individuals access the dark web out of curiosity or for research purposes, exploring this hidden part of the internet without engaging in illegal activities. Users who are properly set could then use the dark web for more privacy-centric communications and transactions. But as stated above unfortunately, the dark web also attracts individuals intending to engage in or facilitate illegal activities due to its anonymity.
The dark web’s existence raises complex ethical and legal questions. It’s a testament to the internet’s decentralized nature, offering both a refuge for those seeking privacy and a challenge for law enforcement. Balancing the benefits of anonymity with the need to combat illegal activities remains a persistent dilemma. It is often viewed through a lens of criminality, is more than a simple black market online. It’s a complex, multifaceted realm that reflects the diverse needs and desires of its users. Understanding this digital frontier requires acknowledging its potential for both harm and good, as it continues to evolve alongside the broader internet landscape.